A Guide to Multi Tenant SaaS Architecture
At its core, a multi-tenant SaaS architecture is a model where one single version of your software serves all your customers, who are called “tenants.”
Think of it like an apartment building. Everyone shares the big, expensive stuff—the foundation, the plumbing, the main electrical grid—but each resident has their own private, locked apartment. This is the exact principle behind most cloud software today. It allows companies to serve a massive customer base from a single, efficient platform.
Why Multi-Tenant Architecture Basically Runs the SaaS World
Look at the tools you rely on every day. Slack. Figma. Your favorite project management app. They all depend on a multi-tenant setup to give a smooth, consistent experience to millions of users at once.
Instead of building a whole separate “house” (a single-tenant instance) for every customer, which would be wildly inefficient, they let everyone share the core infrastructure. This one decision is what makes the SaaS business model so powerful and scalable.
The global SaaS market is absolutely exploding, with some analysts projecting it will hit around $307 billion by 2025. Multi-tenancy is the engine driving a huge chunk of that growth. It allows for massive scale without having to duplicate servers and databases for every new signup. Even better, when you need to push an update or a critical bug fix, you do it once, and everyone gets it instantly. This dramatically slashes your maintenance burden. If you want to dive deeper into market trends, Scalevista.com has some great insights.
Getting the Lingo Down: Key Tenancy Concepts
To really get a handle on multi-tenancy, you need to know three key terms:
- Tenant: This is just a group of users who share access to the software. In 99% of cases, one tenant equals one customer or organization.
- Instance: This is the single, running copy of your entire application—the code, the servers, the databases, all of it. In a multi-tenant world, this one instance serves every single tenant.
- Data Isolation: This is the most important concept of all. It’s the digital wall that ensures a tenant can only see and touch their own data. Even though everyone is technically in the same database, powerful logical barriers prevent any data from crossing over.
A great multi-tenant system makes every customer feel like they are the only person using the app. The shared backend should be completely invisible. All the user sees is their own private, secure workspace.
Comparing SaaS Tenancy Models
Picking the right tenancy model is a huge architectural decision that will ripple through your entire business, affecting everything from your costs and scalability to how much you can customize the product.
The table below gives you a quick rundown of how the main approaches stack up against each other.
Comparing SaaS Tenancy Models
| Attribute | Multi Tenant Architecture | Single Tenant Architecture | Hybrid Architecture |
|---|---|---|---|
| Cost Efficiency | High (shared resources lower costs per tenant) | Low (dedicated resources are expensive) | Variable (balances cost with customization) |
| Scalability | High (easy to add new tenants to existing infrastructure) | Moderate (requires provisioning new instances) | High (can scale different tiers independently) |
| Maintenance | Simple (one update serves all tenants) | Complex (each instance must be updated individually) | Mixed (some shared, some separate updates) |
| Customization | Limited (restricted to configuration, not code changes) | High (can be fully customized for each tenant) | High for single-tenant tier, limited for others |
| Onboarding | Fast (automated and instant) | Slow (requires manual setup and deployment) | Fast for multi-tenant, slow for dedicated |
| Security Isolation | Logical (relies on software to enforce separation) | Physical (data is completely separate in its own instance) | Both (logical for shared, physical for dedicated) |
Ultimately, while single-tenant and hybrid models have their place—especially for massive enterprise clients with unique security or customization needs—the vast majority of SaaS businesses are built on a multi-tenant foundation for its sheer efficiency and speed.
Choosing Your Data Isolation Strategy
Deciding how you’ll isolate customer data is hands-down the most critical architectural choice you’ll make for your multi-tenant SaaS. This decision dictates how you wall off one tenant’s data from another, and it has a massive ripple effect on security, complexity, and your bottom line.
Think of it like this: are you giving each tenant a separate room in one big house, their own floor, or a completely separate building? Each approach has some serious trade-offs.
The diagram below gives you a high-level view of the fundamental fork in the road: the shared (multi-tenant) path versus the dedicated (single-tenant) one.
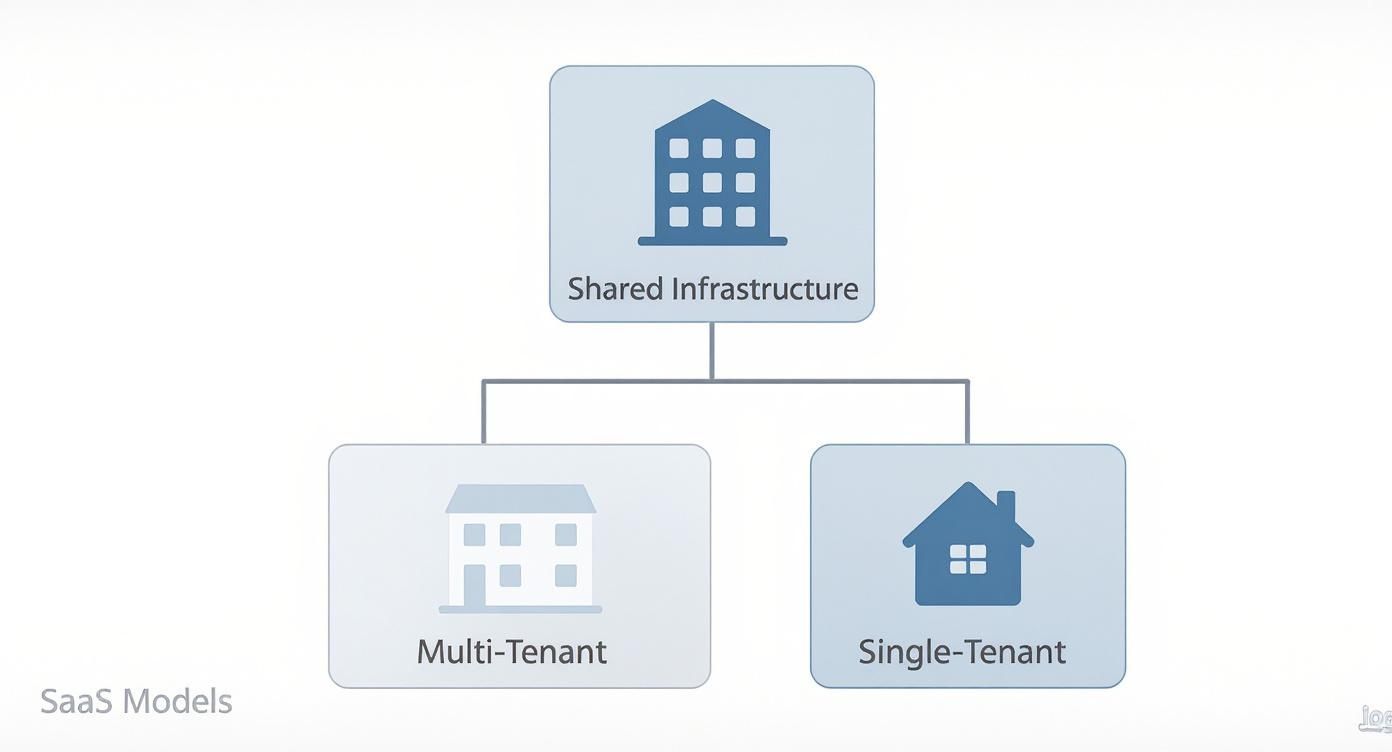
As you can see, both models fall under the “Shared Infrastructure” umbrella. The real difference is that multi-tenancy bets on efficiency, while single-tenancy bets on isolation. Let’s dive into the different flavors of the multi-tenant world.
Shared Database, Shared Schema
This is the default starting point for most SaaS apps, and for good reason. If you’re building an MVP or a startup where speed and cost are king, this is your model. Every tenant’s data lives in the same database, using the exact same tables.
So how do you keep things separate? With a simple but critical mechanism: a tenantId column (sometimes called organizationId) gets added to every table that holds tenant-specific data. This means every single query your application runs must include a WHERE tenantId = 'current_tenant_id' clause.
Crucial Takeaway: Let me be blunt: if you ever miss this tenantId check in a query, you’ve just created a catastrophic data leak. The burden of enforcement is 100% on your application code.
The upsides are obvious: low operational costs and dead-simple management. You have one database to back up, scale, and maintain. But that simplicity comes at a price. You have weaker data isolation and you’re vulnerable to the “noisy neighbor” problem, where one power-user tenant can bog down performance for everyone.
Shared Database, Separate Schemas
This model is a fantastic middle ground. It gives you much stronger data isolation without the headache and expense of managing totally separate databases. Here, all tenants still live on the same database server, but each gets their own dedicated schema (in a database like PostgreSQL) or their own database (in MySQL).
This creates a logical wall between tenants right at the database level. It’s way harder to accidentally leak data because your queries are naturally scoped to one tenant’s schema. This also makes things like tenant-specific backups or data migrations much cleaner.
Of course, it’s not a free lunch. This strategy brings more operational complexity. You have to manage an ever-growing number of schemas as you sign up customers, which can make database migrations and maintenance scripts a bit more fiddly. It’s a smart balance between the simplicity of a shared schema and the iron-clad security of separate databases.
Separate Databases Per Tenant
Welcome to the gold standard of data isolation, often called the “silo” model. Each and every tenant gets their own completely separate database instance. This is the strongest separation possible, making it the go-to for apps that handle highly sensitive data or serve big enterprise clients with strict compliance demands like HIPAA or GDPR.
The benefits are crystal clear:
- Maximum Security: The possibility of cross-tenant data leakage at the database level is zero.
- No More Noisy Neighbors: One tenant’s heavy usage can’t touch another’s database performance.
- Easier Customization: Implementing tenant-specific database changes or extensions becomes trivial.
But this power comes with a hefty price tag. This model is by far the most expensive and operationally complex. Your costs scale linearly with every new tenant because you’re provisioning, managing, monitoring, and backing up a unique database for each one. To get a feel for the kind of tooling this might require, you can check out how to build a powerful database query builder for your internal tools.
Going down this road demands a mature DevOps culture and a solid business case that justifies the much higher cost.
Designing for Performance and Scalability
Nailing your data isolation strategy is a huge first step, but it’s only half the battle. To build a SaaS that people love using, you have to design for speed and reliability from the jump. As your user base balloons, the shared nature of your infrastructure creates some gnarly performance challenges that can bring a poorly designed system to its knees.
The real goal here is to make sure one power-user tenant doesn’t ruin the experience for everyone else. This classic issue, known as the “noisy neighbor” problem, is one of the biggest operational headaches in multi-tenancy. You can’t just react to it; you have to get ahead of it with a smart, multi-layered approach to resource management.

Taming the Noisy Neighbor Problem
Picture this: one of your tenants decides to upload and process ten thousand high-res images all at once. Without any guardrails, that single action could hog every available server resource, leading to timeouts and a sluggish, frustrating experience for every other customer.
Here are the essential strategies you need to keep your shared resources balanced and fair:
- Rate Limiting: This is your first line of defense. Implement strict limits on API calls. For example, you might give a standard tenant 100 requests per minute while an enterprise customer gets 1,000. It’s a simple but effective way to stop abusive or runaway processes in their tracks.
- Asynchronous Job Queues: Never, ever run heavy, long-running tasks like video processing or big report generation in your main application thread. Shove them into a background job queue using tools like RabbitMQ or Redis. This lets them process separately, ensuring your core app stays snappy and responsive.
- Resource Throttling: Go a step beyond simple rate limiting by actively monitoring and throttling resource-heavy operations. If a tenant is running crazy database queries that are dragging the system down, you can dynamically lower the priority of their tasks to protect overall system health.
By 2025, multi-tenant SaaS is set to be the biggest deployment model in the cloud market, mostly because it lets companies get started fast with lower upfront costs. This architectural style helps businesses scale efficiently while keeping costs predictable, which makes solid performance management a non-negotiable for success. You can find more insights on this trend from MarketsandMarkets.
Architecting for Elastic Scalability
Your architecture has to be able to grow and shrink gracefully with demand. This is where modern cloud infrastructure is your best friend. Instead of buying massive servers to handle peak capacity (and letting them sit idle most of the time), you build a system that adapts in real time.
Think about an elastic scaling approach, where your application is broken down into smaller, independent services. For instance, if your file upload service is getting hammered, you can automatically spin up more instances of just that service without messing with the rest of the application. This kind of targeted scaling is way more cost-effective and resilient than trying to scale a giant, monolithic app.
A truly scalable multi-tenant architecture doesn’t just handle more users—it intelligently sends resources where they’re needed most. The system should automatically react to tenant activity, ensuring a fast experience for everyone without over-provisioning and burning cash.
Boosting Speed with Smart Caching
Caching is a secret weapon for cutting down database load and making your app feel lightning-fast. In a multi-tenant world, though, you have to be super careful with how you implement it to avoid accidentally leaking data between tenants.
- Tenant-Aware Caching: Your caching layer absolutely must be designed to store and retrieve data on a per-tenant basis. A common trick is to prefix your cache keys with the
tenantId(e.g.,tenant_123:user_profile:456). - Caching Configurations: Be strategic about what you cache. Frequently accessed, rarely changed data—like tenant settings, user permissions, or custom branding configurations—is the perfect candidate. This saves you from hitting the database on every single request for the same information.
These performance tweaks are especially critical for features like real-time analytics. To see how this applies in practice, check out our guide on building powerful analytics and reporting dashboards that can handle demanding multi-tenant workloads. By weaving together smart scaling, solid resource management, and precise caching, you build a robust multi-tenant architecture that stays fast and reliable, no matter how quickly you grow.
Securing Your Shared Environment
In a multi-tenant SaaS, trust isn’t just a feature—it’s the entire foundation of your business. When customers agree to share infrastructure, they’re placing immense faith in you to keep their data completely isolated and protected. A single security slip-up can shatter that trust and tank your reputation overnight.
This makes a rock-solid security posture non-negotiable from day one.
It all starts with preventing the most dangerous threat: data leakage between tenants. Even a tiny, seemingly innocent bug in your logic can accidentally expose one customer’s sensitive information to another. This is where meticulous, multi-layered security practices become your most valuable asset.

Fortifying Access Control and Permissions
Your first line of defense is a bulletproof Identity and Access Management (IAM) system built for multi-tenancy from the ground up. It’s not enough to just know who a user is; you have to know whose user they are, instantly and constantly.
Every single action, from an API call to a database query, must be checked against the user’s assigned tenant.
This means implementing a Role-Based Access Control (RBAC) system that is inherently tenant-aware. You don’t just have an “Admin” role; you have an “Admin” role within the scope of Tenant A. A user who is an admin for Tenant A should have absolutely zero visibility or permissions in Tenant B, period.
Crucial Insight: Your security model must operate on a “zero trust” basis for tenant context. Assume every incoming request could be malicious or misdirected. You have to verify the tenant at every single layer, from the API gateway all the way down to the final database query.
Preventing Data Leaks with Rigorous Testing
Let’s be real: humans make mistakes. That’s why your development process has to be designed to catch tenant-scoping bugs before they ever see the light of day. Relying on manual testing alone is a recipe for disaster.
Instead, build a security-first culture that makes these practices mandatory:
- Automated Integration Tests: You need a dedicated test suite that does nothing but try to break tenant boundaries. These tests should authenticate as a user from Tenant A and then aggressively attempt to fetch, update, or delete data belonging to Tenant B. If any of these tests pass, your entire build should fail. No exceptions.
- Mandatory Peer Code Reviews: Every pull request that touches data access logic must be reviewed by at least one other developer. The number one priority of this review? Confirming that tenant isolation (
WHERE tenantId = ?) is applied correctly and universally.
Implementing Strong Encryption Strategies
Securing data isn’t just about who can access it; it’s also about making the data itself unreadable to anyone who shouldn’t see it. This means encrypting sensitive data both while it’s flying across the network (in-transit) and while it’s sitting in your database (at-rest).
For enterprise-grade security, consider going a step further with a per-tenant encryption key strategy. It’s more complex to manage, for sure. But using separate keys for each tenant—often managed with services like AWS Key Management Service (KMS)—provides a powerful layer of isolation.
This approach ensures that even in a worst-case scenario where the entire database is compromised, an attacker can’t just use one master key to decrypt everyone’s data.
This strategy is also critical for meeting strict compliance standards. Frameworks like SOC 2, GDPR, and HIPAA have tough requirements for data segregation and audibility. A well-documented security model with strong encryption and detailed audit trails is essential for proving compliance and winning the trust of those high-value enterprise customers.
Putting Your Tech Stack to Work
Alright, enough theory. This is where the rubber meets the road—turning those architectural diagrams into a real, working application. Let’s walk through a practical setup for a multi-tenant SaaS using a modern and scalable stack. Think of this as a solid starting point for your own project.
We’re going to lean on a powerful and popular combo: a PostgreSQL database managed with the Prisma ORM, tenant-aware authentication handled by a service like Clerk, and subscription billing powered by Stripe. This stack gives you a rock-solid foundation for building something secure and ready to grow.
Database and Data Access with Postgres and Prisma
PostgreSQL is a fantastic choice here, mainly because it has robust support for things like row-level security (RLS) and schema separation right out of the box. When you pair it with Prisma, an open-source ORM, wrangling tenant data becomes way simpler and a lot less error-prone.
The real magic happens with Prisma’s middleware and client extensions. These are game-changers for enforcing data isolation at the application level. You can write a single piece of logic that automatically tacks on the crucial WHERE tenantId = '...' clause to every single database query.
Key Advantage: This approach slashes the risk of accidentally leaking data between tenants. Instead of relying on every developer to remember to add that filter to every query they write, the ORM handles it automatically. It’s a powerful security backstop built right into your data access layer.
This strategy is particularly effective for the shared-database, shared-schema model. It delivers strong, application-enforced isolation without the operational headache of managing separate databases or schemas for every customer.
Handling Authentication and Tenant Context
In a multi-tenant app, authentication isn’t just about checking a password. It’s about immediately locking a user into their correct tenant context. From the moment they log in, their session has to be securely tied to their specific organization or workspace.
Services like Clerk or Auth0 are built for this exact problem. They let you attach metadata, like a tenantId, directly to the user or session object.
Here’s what that flow typically looks like:
- A user signs in.
- The auth service (like Clerk) creates a secure JSON Web Token (JWT).
- This JWT isn’t just a generic token; it contains a custom claim, like
{"tenant_id": "acme-corp-123"}. - Your backend gets this token with every request, checks that it’s valid, and pulls out the
tenant_id. - That ID becomes the source of truth for everything that follows—database queries, API calls, you name it. This ensures the user is always playing in their own sandbox.
This method centralizes how you identify a tenant, making it super reliable and easy to manage across your entire application. This even extends to things like user documentation. For anyone looking to build robust, tenant-aware guides, we’ve got some resources on creating secure API documentation and developer portals.
Integrating Stripe for Tenant-Specific Billing
Last but not least, every SaaS needs to get paid. Stripe is the undisputed champ here, offering powerful APIs to handle even complex billing logic on a per-tenant basis. The process is straightforward: when a new organization signs up for your app, you create a corresponding Customer object in Stripe.
You’ll want to store the StripeCustomerId you get back in your own database, right alongside that tenant’s record. This link is the key to managing everything for that customer, from their monthly subscription to any metered, usage-based billing.
When a tenant decides to upgrade or change their plan, you just grab their stored StripeCustomerId and use it to tell Stripe what to change. This keeps all the billing logic cleanly separated from your core application code and guarantees each customer is billed accurately and independently.
This model is fundamentally changing how entire industries operate. Take product lifecycle management (PLM) platforms, for instance. Multi-tenant SaaS is fueling a new generation of cloud-based PLM systems where multiple companies and their suppliers can collaborate on a single platform. The centralized infrastructure drives down costs and ensures everyone is always working with the latest version. You can find more insights on how multi-tenancy is reshaping PLM on OpenBOM.com. By pulling these tools together, you can build a secure, production-ready foundation for your own multi-tenant application.
Common Questions About Multi-Tenant Architecture
When you start digging into multi-tenant SaaS, the same questions pop up time and again for developers, founders, and architects. Getting straight answers is key to making a call that will define your app’s future. Let’s tackle the most common ones head-on.
We’ll get into the real-world answers on the challenges, migrations, customization, and figure out when this model is the right—and wrong—choice for your business.
What Is The Biggest Challenge In Building A Multi-Tenant SaaS Application?
Hands down, the single biggest challenge is nailing strict data isolation and security between tenants. It’s the one thing you absolutely cannot get wrong.
While sharing infrastructure saves a ton of money, a single slip-up in your logic can cause a catastrophic data breach, showing one customer’s private data to another. This is the stuff of nightmares for a SaaS company.
It means you have to obsess over your design from day one. You need rigorous, automated tests that are constantly trying to punch holes in your tenant walls. And you need continuous security monitoring. Getting this right is the absolute foundation of a trustworthy multi-tenant app.
A close second is the “noisy neighbor” problem. This happens when one hyper-active tenant hogs all the resources, slowing down the experience for everyone else. Taming this requires smart resource management, rate limiting, and constant monitoring to keep things fair and fast for all your customers.
Can I Switch From Single-Tenant To Multi-Tenant Architecture Later?
Technically, yes. But you really, really don’t want to. It’s an incredibly complex and high-risk migration. Moving from a single-tenant setup (where every customer gets their own separate database and app instance) to a shared multi-tenant model is a monster of a project.
The process involves:
- Wrangling and consolidating potentially hundreds of separate databases into one shared system.
- Rewriting your application’s core logic so every single function is “tenant-aware.”
- Completely re-engineering your auth and permission systems to manage shared access securely.
This kind of migration almost always involves significant downtime and a massive risk of data corruption or security holes if it isn’t executed perfectly. It’s almost always cheaper, safer, and saner to design for multi-tenancy from the start if you think it’s even a remote possibility for your product.
Key Takeaway: Migrating from single to multi-tenant is like trying to rebuild the foundation of a skyscraper while people are still working on the 50th floor. It’s an expensive, dangerous project that’s best avoided by planning ahead.
How Does Multi-Tenancy Affect Customization Options For Customers?
Multi-tenancy puts natural guardrails on deep, structural customization. Since everyone is sharing the same core application and database, you can’t let one tenant rewrite the source code or change the database schema.
Instead, customizations are usually limited to what can be configured through the UI or API.
This usually covers things like:
- Branding: Letting customers upload their own logos and pick their color schemes.
- Permissions: Setting up custom user roles and access controls.
- Data Models: Adding custom fields to existing objects (like a contact or a project).
- Workflows: Tweaking business logic using pre-defined rules or triggers.
What it doesn’t allow for is custom code or fundamental database changes for just one tenant. This is the core trade-off. Customers give up that deep customization in exchange for much lower costs, automatic updates, and zero maintenance on their end.
Is Multi-Tenancy Suitable For All SaaS Products?
Absolutely not. It’s a fantastic model, but it’s not a silver bullet.
Multi-tenancy shines for apps serving a broad market where most customers have similar core needs. This is where the economies of scale give you a massive competitive edge. Think of CRMs, project management tools, or email marketing platforms.
But it can be a terrible fit for products that demand unique requirements, such as:
- Extreme Customization: Apps that need to be heavily tailored with custom code for each client.
- Strict Data Sovereignty: Clients whose data, for legal or policy reasons, absolutely must be stored in a specific country or on a dedicated server.
- Enterprise Security Policies: Big enterprise customers who have iron-clad internal policies forbidding any kind of shared infrastructure.
For these use cases, a single-tenant or even a hybrid model—where you offer multi-tenancy for your standard plans and dedicated instances for enterprise tiers—is a much smarter approach. You have to know your target market’s needs before you commit to an architecture.
Ready to build a secure, scalable, and AI-ready SaaS without the DevOps nightmare? saasbrella provides a complete, production-grade foundation with multi-tenancy, billing, and auth pre-configured so you can focus on building your product, not your infrastructure. Learn more and get started at saasbrella.co.